The Holy Grail of Cloud Security
Gartner states that security continues to be the biggest inhibitor of cloud adoption. This is not a surprise because cloud services are shared, always connected and dynamic environments by nature, making them a challenge when it comes to security.
On-premises IT security controls do not touch the cloud, leaving customer data at risk from the same types of threats targeting assets and applications in corporate data centres. What’s more, malware introduced into the cloud can easily propagate among VMs, attack virtual segments or even ride unimpeded over VPN links back to corporate networks.
Public cloud networks are built upon a unified, multi-tenant platform using a shared infrastructure to support millions of simultaneous customers. Foundational to public cloud environments are enhanced security, operational management and threat mitigation practices that protect the infrastructure, cloud fabric, hypervisors, services and tenant environments.
While public cloud providers deliver strong security controls to protect the cloud fabric, they have no knowledge of “normal” customer traffic and thus are unable to determine malicious content from benign. This presents a big challenge to security administrators to provide the same security protections against the latest fifth generation (GenV) cyber-attacks targeting the cloud as they do on-premises. A defence-in-depth strategy for the cloud should also include protecting all workloads and data from exploits, malware and other sophisticated attacks.
These emerging technology trends, with their increased agility, flexibility and efficiency, also give rise to new security challenges:
The static security policy: The private cloud is a dynamic environment. New applications are instantly deployed, the environment scales up and down and applications move around the data centre. Security services must keep pace with these rapid changes and consider elastic scaling. This requires automation, otherwise security will either be neglected or become a bottleneck in the process of provisioning applications.
Internal traffic visibility: Private clouds and their mobile workloads mean a shift in data traffic growth inside the virtualised data centre. In addition to protecting traffic inside and outside of the data centre, virtualised networks’ security must also be able to inspect and enforce security policies for traffic moving inside the data centre.
Limits of traditional segmentation: Traditionally, security segments have been tightly coupled with the physical network topology. This resulted in exceedingly manual, process-intensive networking configurations. However, deploying security within virtualised environments means these physical boundaries are now logical and automated, adversely impacting static network security processes, contributing to operational overhead and impacting network agility.
Advanced threats: Sophisticated, fifth generation (GenV) cyber-attacks target the weakest systems on the network. They obtain control of the infected machine using a Command and Control (C&C) server and then move from virtual machine (VM-to-VM) to steal valuable data without ever being detected. The threats are no longer just at the network perimeter and so advanced protection is also needed to minimise and mitigate post-breach propagation within the data centre.
It is essential for security to overcome the challenges outlined above and integrate with SDN architectures, network virtualisation and orchestration platforms. The solution must be built on five key principles:
- Automated security services insertion into the network. Security service-chaining enables security for all traffic in the data centre automatically. Now we can create security policies that implicitly configure the network in the background.
- Policy and context-awareness. Understand the state of the applications and the context by integrating into cloud orchestration and IT tools, like ticketing systems, user directories and SDN controllers. Learn and apply the best policy based on state and context. This also enables secure, scalable deployments and allows you to grow the number of data centre applications safely.
- Trusted automation and orchestration. To effectively enable automation, it needs to be trusted. Trust-based APIs enable self-service integrations with third-party systems and automate policy changes within the scope of their privileges. This means administrators can allow changes to specific rules within the policy.
- Compliance and threat visibility. If a compromised virtual machine is detected, it must be quarantined with options for remediation. Reporting and analytics are necessary to uncover and understand traffic trends.
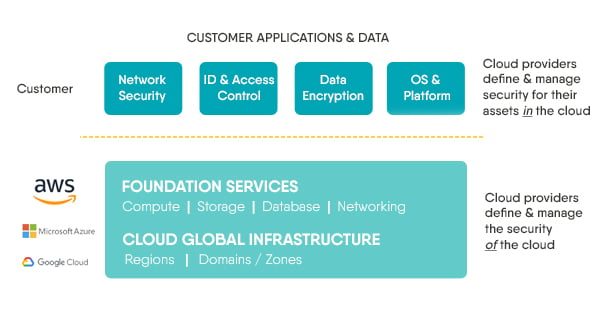
- Centralised management. Security management is simplified with unified administration and monitoring of physical and virtual security gateways, and public IAAS such as AWS, Azure, Google Cloud Platform and more.Understanding the customer responsibility role versus the role of IaaS providers helps organisations make the best decisions concerning the security of their cloud environments. It also ensures that an organisation’s cyber security strategy efficiently and cost-effectively aligns with the rest of the business goals while delivering consistent protections for all corporate data both on-premises and in the cloud.
Presidio, in conjunction with our security partners such as CheckPoint, Fortinet or Cisco can help you achieve this objective.



